
Did one already visit your hard disk to your insue?
You could believe the stupid question and could tell you that it is not necessary to be paranoiac on the net.alors you are stupid and naive.
I go you show some things. Useless to write me to ask me of the Trojan or the methods of hacking, I am against it (except some very particular cases)!!!
These few pages are had informative goal, I don't use these software that on my own computers (I have luck to have 2 and 2 telephone lines of it), or on those that essayent to come to see on my computer (the watered waterer).
It applies to the reader who will understand that he/it is himself can be made already have and how that works.
How to know the name of a machine?
Many software underground that allows it to you exists I have 2 that make it very very well of them. You bring the IP address in and you have the result in 3 seconds.
Yes but how to have this IP address?
Some software scannent all Ip addresses ex "takes ip" or a classic IP scaner.
On IRC it is cool.servez you.
To know the IP address of a connected on IRC or ICQ is easy, on IRC, you hit the order / pseudo dns and you are going to see in "Status." If the connected omitted to hide the one here, she/it will appear, if it is not the case you will have his/her/its server's name by ex: aaa-333-44-wanadoo.fr, not of panic!! open a MS-DOS window and hit the following order :
ping - has 333-44-wanadoo.fr
you will have his/her/its IP address then.
On ICQ, you go in your list of contacts, you click then on the pseudo on info, if the user hid his IP you will see to appear N/A, not of problem!! Let the window open "info", put your ICQ on "off line" close the window "info" recliquez on the pseudo reopen the window "info", his/her/its IP becomes visible.
How does to reach have distance on a computer?
It is necessary for that, that in the configuration network of the computer to which you want to reach, selected "Customer for the networks microsoft" and "Sharing of the files" (Start / panel of configuration / Network).
Open a MS-DOS window, hit the following order then:
nbtstat - TO ip of the computer
You are going to see to appear:
NetBios Remote Machine Name Table
Name Type status
-----------------------------------------------------------------
-----------------------------------------------------------------
yannick < 00 > UNIQUE Registered
yannick < 00 > GROUP Registered
MAC Adress = 43-22-12-69-28-37
Only the line "yannick < 00 > UNIQUE Registered" interests us, you now know that "yannick" is the name of the distant computer
hit the order:
edict 1mhosts
you are in the publisher back, there you hit :
ip of the computer "yannick"
Save and leave the publisher, back on Back hit :
nbtstat - R
you get:
Successful purges and preload of the NBT Remote Cache Name Table.
You are now on the hard disk of the distant computer, you can, to return under Windows, to Start / to search for / computer and hit yannick \ \ note the given path well.
Go then in the explorer and in the menu Opted / to connect a reader network hits the access path to the computer. Windows affects you a reader (D for example) that correspond to the hard disk of the distant computer.
The horses of troie
This technique permits to take the control of a computer, to visit it, to use, to suppress the file or a dur.et disk of other things funnier as to open the reader cd rom etc.
To infect you has several solution.la first that is to go on a site as the one the and to tell people "you is rings of all quote but has a software that cva to recover if you are pestilential etc."
In fact one puts you a server in bottom without you didn't realize from it.
One can also download a program and strange you have a message telling you that the file lambda is untraceable. (makes you of it have just put a Trojan).
Winnuke: you go nuker (it is has say to eject those that embarrass you), in fact it is you that you are made nicker while putting a Trojan.
One will warn you as telling you this software can be to detect by norton or mc affe because he/it doesn't make the difference between the good and the bad, but have false crainte.c'est!!!
Some exists numerous my favorites being netbus (really funny and efficient), back opening (the worse because he/it gives all your passwords and internet access code.), the thing, subseven, etc.
A Trojan divides in 2 :
A server (target has infested)
A customer (the one that directs)
Some make themselves have while wanting to play the sorcerer's apprentice because they install the 2!!!!!!!!!!!!
The server is adjustable and you can program it so that he warns you of the that your prey is on line.
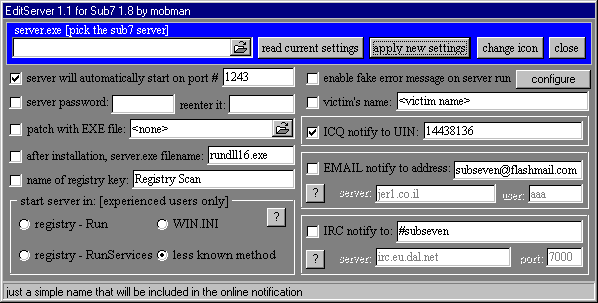
Here is a server of subseven :
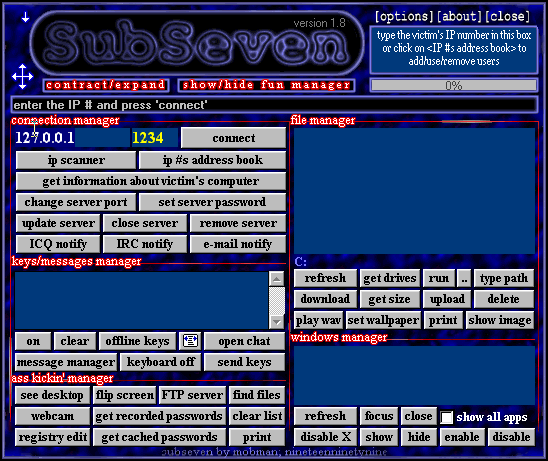
here is the customer :
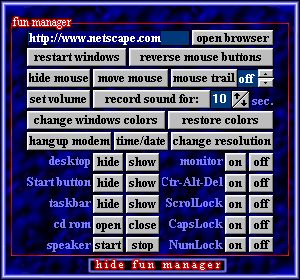
the quotes fun :
How to protect itself/themselves?
In the first place to make the acquirement of a firewall marks norton that tells you everything that between and fate of your PC, that is worth in the 500 francs and that should be obligatory, you will be surprised surely to see it.
Then nothing to download on unofficial sites, even if it is tempting or assume it then!!!
Finally to put has day his/her/its antivirus.
Information: it is while knowing all it that you will protect yourselves best.
Don't believe that it is on average a mythe.j'ai 30 attacks per days whereas I don't have any server on my computer.
To good entendeur...
If you think to have a horse of troie, I can the verrifier, it is sufficient to send me a promenade while telling me what makes you think it.

Return has the home page

all copillage will be pursued before the courts

00036468